FUTUREISNOWN:
CRITICAL AND SPECULATIVE PROTOTYPING AS A FORM OF ART.
We are data.
Being constantly connected to global, informational and technological processes, it comes as no surprise
we cannot imagine life without communication, the web, social networks and instant messengers.

Every second, Google is asked 40,000 questions, 50,000 messages are sent via Facebook, more than 5 hours of video content are uploaded to YouTube. With so much generated data, the access to it, its processing, storage and the ways to use it acquire new meaning.
We are rapidly merging into a new digital era, informational and
technological reality, bringing our
conflicts, systemic crises and critical
points with us. The boundaries between
our digital and physical identities are
gradually blurred, technology becomes
a more seamless part of our life. We no longer know and cannot imagine
where we are moving according to the global coordinate system, and
how objects, personal data, messages,
photos, preferences and biomarkers are
being formed into databases connected
to billions of other people, kettles
and computers. We do not have time to learn about it, we are always in a
hurry and too busy for our own good,
responding to emails and messages,
talking on the phone, following people
on social networks and sharing our own
lives. We are in a constant flow of data
and so we merge with it. We become a
part of it.
Web search data is a valuable source of information. We are extremely close and personal with the search engine and we never hesitate to share our thoughts, ideas and secrets with it. It knows what we are looking for and remembers it better than us. Whenever we visit a website, send a message, answer buzzfeed quizzes, we leave digital traces that identify us and help assign personal markers of behaviorto us.
A mobile phone keeps track of where its owner can be most often found during work hours and where he spends his free time, and if he even has a job. It knows what he eats and how much time he spends in a nearby cafe. The accumulated data is processed
Web search data is a valuable source of information. We are extremely close and personal with the search engine and we never hesitate to share our thoughts, ideas and secrets with it. It knows what we are looking for and remembers it better than us. Whenever we visit a website, send a message, answer buzzfeed quizzes, we leave digital traces that identify us and help assign personal markers of behaviorto us.
A mobile phone keeps track of where its owner can be most often found during work hours and where he spends his free time, and if he even has a job. It knows what he eats and how much time he spends in a nearby cafe. The accumulated data is processed
in a way
it can create a more complete picture
of us than we could imagine. Amazon
already knows what we want and need
before we realize it ourselves.
The Wi-Fi smartphone identifier and RFID tag on the social map can be read at the store entrance, so the sales manager can find out the income level and potential interests of the visitor. Data is used to determine age, gender, race, and predict sexual preferences, relationship status, political views, and other perceptions, behaviors, and needs.
Back in 2011, Max Schrems asked Facebook to provide him all the information the company had about him. Only after the trial he received a CD with a 1200-page PDF document that contained information about his friends, screenshots of pages he has liked or mentioned, all the advertisements that he had scrolled through [1].
In 2017, French journalist Judith Duportail requested all the information a dating app Tinder had about her. She received an 800-page document with all the texts and information about her interests and preferences. All the men that she swiped right; all 1,700 messages she had sent since 2013; when the account was set up; her Facebook likes; Instagram pictures; information about her education. Sexual preferences and her deepest secrets [2]. What if this data is hacked, lost or sold to third parties?
The Wi-Fi smartphone identifier and RFID tag on the social map can be read at the store entrance, so the sales manager can find out the income level and potential interests of the visitor. Data is used to determine age, gender, race, and predict sexual preferences, relationship status, political views, and other perceptions, behaviors, and needs.
Back in 2011, Max Schrems asked Facebook to provide him all the information the company had about him. Only after the trial he received a CD with a 1200-page PDF document that contained information about his friends, screenshots of pages he has liked or mentioned, all the advertisements that he had scrolled through [1].
In 2017, French journalist Judith Duportail requested all the information a dating app Tinder had about her. She received an 800-page document with all the texts and information about her interests and preferences. All the men that she swiped right; all 1,700 messages she had sent since 2013; when the account was set up; her Facebook likes; Instagram pictures; information about her education. Sexual preferences and her deepest secrets [2]. What if this data is hacked, lost or sold to third parties?
Privacy is the new luxury.
My privacy is no longer a fundamental right and so it becomes a luxury. My idea of the value of personal data as a resource has not yet been formed in the metaphysics of my personality. I am not yet aware of the importance, real value and availability of this data. Perhaps because I cannot feel it physically, touch or perceive it. I, myself, have become data.
![]()
disagreeable to those who manage these systems. And it is important to remember. Moreover, it is important to ask the question - is the data stored safely and is it inaccessible to third parties, how safe it is from being sold, abused and illegally used?
My privacy is no longer a fundamental right and so it becomes a luxury. My idea of the value of personal data as a resource has not yet been formed in the metaphysics of my personality. I am not yet aware of the importance, real value and availability of this data. Perhaps because I cannot feel it physically, touch or perceive it. I, myself, have become data.
disagreeable to those who manage these systems. And it is important to remember. Moreover, it is important to ask the question - is the data stored safely and is it inaccessible to third parties, how safe it is from being sold, abused and illegally used?
Artist project. Prey. Data - is a new oil.
About privacy, security and our network experience.
Program for removing geolocation data, wi-fi connection data, device used info, camera photos, screenshot from laptop, Video. 2016. Anton Bundenko, link
I do not ask myself about how and
where this data is stored. Whether it can or cannot be hacked. Who and how monitors its security so it
does not find its way into the hands
of third parties. What is the statu of those who own the data and how
can corruption schemes and possible
abuses be read and monitored. How I can sell and buy data, and whether
my data can be obtained by interested
parties.
Where and at what amount of data
does personal information become impersonal? Let’s imagine I am heading to a business center for a meeting. All of my personal information – temperature, sweating, facial expressions, motility – determining the degree of excitement, characterizing decision-making, etc. could be accessed by my business partner before and after the meeting. Is it still mine or already public? With how many people should I mix, when entering the business center, so that our data collected together is no longer personal and becomes statistics?
New reality.
My smart home speakers, Amazon Echo and Google Home, know that on Monday mornings I wake up 15 minutes later, so they immediately send a signal to the kettle on the first floor of my apartment. They know that today I want my tea to have a temperature of 36.2 degrees, that I would prefer wearing a business suit, and with a 68.7% probability I will forget my car keys. Because of disturbed sleep and my tight business schedule, which forms additional distractions, or because, apparently, I fell in love with a girl, sitting next to me in a cafe yesterday, and I cannot get her out of my head.
Where and at what amount of data
does personal information become impersonal? Let’s imagine I am heading to a business center for a meeting. All of my personal information – temperature, sweating, facial expressions, motility – determining the degree of excitement, characterizing decision-making, etc. could be accessed by my business partner before and after the meeting. Is it still mine or already public? With how many people should I mix, when entering the business center, so that our data collected together is no longer personal and becomes statistics?
New reality.
My smart home speakers, Amazon Echo and Google Home, know that on Monday mornings I wake up 15 minutes later, so they immediately send a signal to the kettle on the first floor of my apartment. They know that today I want my tea to have a temperature of 36.2 degrees, that I would prefer wearing a business suit, and with a 68.7% probability I will forget my car keys. Because of disturbed sleep and my tight business schedule, which forms additional distractions, or because, apparently, I fell in love with a girl, sitting next to me in a cafe yesterday, and I cannot get her out of my head.

My smart home speaker knows that I do not completely agree with the current government and ruling elite, and sometimes I am even thinking of changing something drastically. This is already enough for an officer of the X department to send me a subpoena or a request to the Investigation Committee, citing my thoughts, social network posts and controversial texts, no matter how long ago I wrote them.
My smart speaker is connected to the technical, service and home appliances of the Internet of Things or the Internet of everything – a voice assistant, like Siri, only with a physical presence, which listens to me constantly to learn more about my preferences and interests. This small speaker can inform me about the weather, report news, read poems or a couple of paragraphs from the civil code, make a to-do list, and perform any other tasks. It is a very good listener and conscientiously records all my interactions with it, sends them back for analysis and receives updates to become more interesting and convenient. Sometimes it records not only my contacts with her, but also random extraneous noises in the apartment or room.
I can be sure that if a burglar bursts into my
apartment, it will recognize him and
give an emergency signal to the police
control panel. But there is a possibility it
will work against its owner. In 2016, one
of these speakers sent her owner to jail,
speaking in court as a witness in a case
of homicide. Soon such speakers will be
everywhere, some of them will become
writers, lawyers or even psychologists.
![]()
In the city, I leave digital footprints everywhere through bank cards, smartphones and smart bracelets. I am seen by CCTV that recognizes me by movement and face. AI identifies
my political views, intelligence, predisposition to illegal actions, specific character traits and other personal information that I myself may not be aware of. The problem is that sometimes such programs already have the human factors of racism, xenophobia and hatred built in.
Intelligence agencies and politicians tend to abuse surveillance systems, using them to identify the opposition –¬ people with certain political beliefs, people who are friends with members of secret communities, people who attend meetings, rallies or even visit anti-government websites.

In the city, I leave digital footprints everywhere through bank cards, smartphones and smart bracelets. I am seen by CCTV that recognizes me by movement and face. AI identifies
my political views, intelligence, predisposition to illegal actions, specific character traits and other personal information that I myself may not be aware of. The problem is that sometimes such programs already have the human factors of racism, xenophobia and hatred built in.
Intelligence agencies and politicians tend to abuse surveillance systems, using them to identify the opposition –¬ people with certain political beliefs, people who are friends with members of secret communities, people who attend meetings, rallies or even visit anti-government websites.
the social control, which is now fully implemented in China. In these practices, false alarms are often inevitable, and the outcome can be tragic. Considering the predictions of what I can potentially do in the future, an adjustment is made to my present in the form of preventive work and other instruments of influence.
What is useful fighting against criminals, in fact turns into persecution of any dissent and critical judgments, disagreeable to those who manage these systems. And it is important to remember. Moreover, it is important to ask the question - is the data stored safely and is it inaccessible to third parties, how safe it is from being sold, abused and illegally used?
This new reality, in which we find ourselves, has its pros and cons. It would be a mistake to consider all its problems technological only. If we live in an informational technological era, it is vitally important for us to understand how it functions and what processes affect us. Therefore, I walk to my office through the informational flows of the big city, take a turn into the alley, take the freight elevator, pull a gadget out of the data blocking pocket, take off the Electrosmog shirt and find myself in Futureisnown. Here I am, doing things from the future in the present.
Artist project. Prey. Data - is a new oil.
About privacy, security and our network experience.
Program for removing geolocation data, wi-fi connection data, device used info, camera photos, screenshot from laptop, Video. 2016. Anton Bundenko, link
Futureisnown.
We, the project participants, see our mission in informing about hidden processes around us and in educational activities.
Our duty is to educate others in terms of informational and technological processes regarding the new reality that affect us daily.
We deliberately use certain mediums and end-use products for possible personal experience. We believe that only exhibitions and educational events in museums, galleries, funds and fairs cannot work productively and carry out educational tasks, in a way using the tools, mediums and practices that we have come up with altogether can.
We start with a detailed study of the technological and scientific contexts. Their potential use or real use in modern commercial and socio-political spheres.
Based on the results of the research, real and speculative scenarios, Futureisnown creates objects of the future reality in the present, expanding the functionality of already existing things, filling them with new meaning.
This is a design of a functional that does not exist yet but will become relevant in the near future.
Futureisnown works in three formats of information: 1 - Informational design, 2 - Critical design, 3 - Functional design.
1 - Informational design.
Information design is any informational object: both digital (web-narrators, informant websites) and physical (vandal stickers with information about preventive control, links to important sites and articles, informational hoodies with info about post-truth and other processes of new reality). This is a developing educational game in reality, where the owner of an information officer’s sweatshirt begins to inform others through vandal stickers and other objects of communication, sending links to websites and web- tellers, which are updated in digital space and merge with the physical space.
![]()
Examples of the Informational design. Telegram
informational chanal, web informational platforms,
informational futureisnown officer sweatshirt, vandal stickers.
Information design is any informational object: both digital (web-narrators, informant websites) and physical (vandal stickers with information about preventive control, links to important sites and articles, informational hoodies with info about post-truth and other processes of new reality). This is a developing educational game in reality, where the owner of an information officer’s sweatshirt begins to inform others through vandal stickers and other objects of communication, sending links to websites and web- tellers, which are updated in digital space and merge with the physical space.

2 - Critical design.
Critical design is presented through fictional objects based on speculative scenarios of a potential future, which, in turn, are drawn from actual and real facts and signals in the present. The design of the functions, that may soon be relevant. Or an absurd narrative, which sometimes turns out to be a reality. These objects are made in a way that it is often impossible to distinguish their “real” reality from its speculative reality.
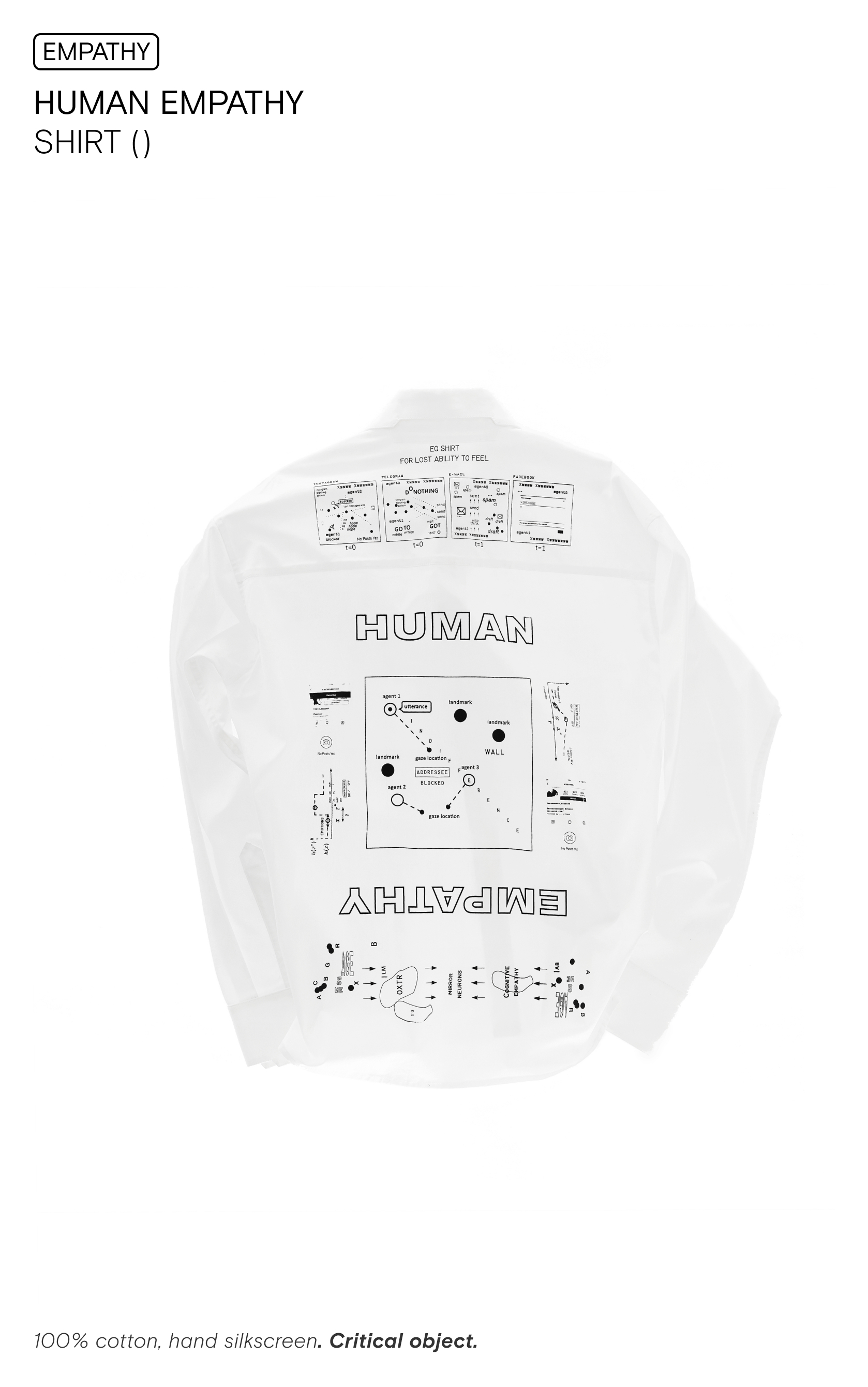
They are formed from studies, reflection on which turns the idea of many familiar things upside down. The purpose of critical design is to form critical thinking and raise very important topics through “playing” with these objects via personal use. These can be shirts, allowing a different perception of Hertz space aroun us, protecting against unauthorized access to personal information and electrosmog-pollution, belts for storing personal data during digital transfer, and VPN connection and the formation of secure networks bags.
![]() Electrosmog protected shirt.
Electrosmog protected shirt.
Critical design is presented through fictional objects based on speculative scenarios of a potential future, which, in turn, are drawn from actual and real facts and signals in the present. The design of the functions, that may soon be relevant. Or an absurd narrative, which sometimes turns out to be a reality. These objects are made in a way that it is often impossible to distinguish their “real” reality from its speculative reality.
They are formed from studies, reflection on which turns the idea of many familiar things upside down. The purpose of critical design is to form critical thinking and raise very important topics through “playing” with these objects via personal use. These can be shirts, allowing a different perception of Hertz space aroun us, protecting against unauthorized access to personal information and electrosmog-pollution, belts for storing personal data during digital transfer, and VPN connection and the formation of secure networks bags.
 Electrosmog protected shirt.
Electrosmog protected shirt.
3 - Functional design.
Functional design is the development of critical design, when the fictional critical functionality turns out to be real and really working, such as sweatshirts with an anti-globalization pocket and blocking cellular communication, Wi- Fi, Bluetooth, radio, geolocation and other frequency waves for temporary entry into privacy zones, acquainting us with switches between digital and physical and ethical gestures of digital culture.
![]() 15min Offline pocket. Blocking cellular, wi-fi, Bluetooth, geolocation,
radio and other electromagnetic waves from civil to
military. Use for temporary entering to the Pause.
Rubber, blocking technology, cotton, magnet,
silkscreen, 2016-2017. link
15min Offline pocket. Blocking cellular, wi-fi, Bluetooth, geolocation,
radio and other electromagnetic waves from civil to
military. Use for temporary entering to the Pause.
Rubber, blocking technology, cotton, magnet,
silkscreen, 2016-2017. link
Personal experience.
All the objects form an informational field and are designed for a living experience. This is extremely important for Futureisnown. The ability to get live and personal experience while using these objects and garments and playing with them is a more effective tool for raising awareness. In order to do this, Futureisnown uses the intervention of speculative reality objects in the world of commercial products.
Functional design is the development of critical design, when the fictional critical functionality turns out to be real and really working, such as sweatshirts with an anti-globalization pocket and blocking cellular communication, Wi- Fi, Bluetooth, radio, geolocation and other frequency waves for temporary entry into privacy zones, acquainting us with switches between digital and physical and ethical gestures of digital culture.
 15min Offline pocket. Blocking cellular, wi-fi, Bluetooth, geolocation,
radio and other electromagnetic waves from civil to
military. Use for temporary entering to the Pause.
Rubber, blocking technology, cotton, magnet,
silkscreen, 2016-2017. link
15min Offline pocket. Blocking cellular, wi-fi, Bluetooth, geolocation,
radio and other electromagnetic waves from civil to
military. Use for temporary entering to the Pause.
Rubber, blocking technology, cotton, magnet,
silkscreen, 2016-2017. linkPersonal experience.
All the objects form an informational field and are designed for a living experience. This is extremely important for Futureisnown. The ability to get live and personal experience while using these objects and garments and playing with them is a more effective tool for raising awareness. In order to do this, Futureisnown uses the intervention of speculative reality objects in the world of commercial products.
Artist project. Prey. Data - is a new oil.
попробуй вставить кусочки из видео про создание брнеда сайт и мероприятия движ весь - Video с Air Moscow / как подписываешь / с шоурума кусочек /
A data, device used info, camera photos, screenshot from laptop, Video. 2016. Anton Bundenko, link
Themes and Objects. Убрать чать фотоиллюстраций
Futureisnown. (Theme 01)
The first topic Futureisnown
addresses is the issue of preventive personalization, control and targeting [3]. The future here is being modified in the present even before this present has come. With the help of analytical companies, corporations offer a subjective present that models an ideal subjective future, building on personal search queries and Internet actions in the past. Placing us in filter bubbles, algorithms of companies, social and political institutions are aware of our desires and interests even before we realize them.
![]()
Futureisnown. (Theme 01)
The first topic Futureisnown
addresses is the issue of preventive personalization, control and targeting [3]. The future here is being modified in the present even before this present has come. With the help of analytical companies, corporations offer a subjective present that models an ideal subjective future, building on personal search queries and Internet actions in the past. Placing us in filter bubbles, algorithms of companies, social and political institutions are aware of our desires and interests even before we realize them.

This website allows me to check all the
active companies of the alliance that
collect, stack and process my actions
in my web browser: http://www.
aboutads.info/choices/. Then they sell
them to PR companies that collect
personalized native advertising for me,
to political technologists who offer me personalized content I would like
to see. Sometimes, there are leaks or
hacks, and the data becomes available
to attackers and third parties.
Similar processes are actively used in social and political contexts. In geopolitics, preventive strikes are performed on the terrain or targeted strikes, often turning out to be inaccurate.
![]()
On the informational sweatshirts you can find more information about it. The vandal stickers that cannot be ripped off share a link to http://www.aboutads.info/choices/,
Similar processes are actively used in social and political contexts. In geopolitics, preventive strikes are performed on the terrain or targeted strikes, often turning out to be inaccurate.

On the informational sweatshirts you can find more information about it. The vandal stickers that cannot be ripped off share a link to http://www.aboutads.info/choices/,
where you can learn
more about companies that collect all
our actions in the browser for native
advertising and decline access to your
actions. There is also a telegram channel
where important facts and links to
software and important projects are
published.
![]()
Critical – presents objects of speculative design that only have a fictional functionality but raise important questions about the potential need of this functionality. One of the objects of critical design is a personal belt for safe high-speed transfer in the digital space.

Critical – presents objects of speculative design that only have a fictional functionality but raise important questions about the potential need of this functionality. One of the objects of critical design is a personal belt for safe high-speed transfer in the digital space.
 Post-digital safety belt Fasten your belt to protect personal data during the
transition to the post-digital society. 2017, sling, rubber, metal buckle, engraving, silkscreen. link.
Post-digital safety belt Fasten your belt to protect personal data during the
transition to the post-digital society. 2017, sling, rubber, metal buckle, engraving, silkscreen. link.Just as a driver fastens a belt for safe speedy movement in a physical space, a person uses this belt for safe speedy transfer in a digital space, keepin his data, privacy rights and personal baggage during the flight.
It seems absurd but given the amount of information that third-party applications collect about us and which we do not think of sharing during setting up our accounts, we start thinking there is an actual need for this object.
Electrosmog (Theme 02)
The next topic studied by Futureisnown is Electrosmog. Around us there i a huge number of electromagnetic waves of a different spectrum, most of which are not visible to us. If our eyes could tune into the waves of invisible frequencies, all electronic objects will not only look different but their borders will spread much wider, merging with other objects. The perception of the world will change. A new physical environment called Hertz space will be formed.
![]()
In large metropolitan areas, i places where the number of stream of information exceeds the limit, the locations of Electrosmog are
determined. To do this, we developed
a special shirt for movement in the
aggressive information environment
«Electrosmog» in the electrogeography
of the metropolis, which allows you to protect its user from electrosmog
pollution and unauthorized access to
personal information.
The next topic studied by Futureisnown is Electrosmog. Around us there i a huge number of electromagnetic waves of a different spectrum, most of which are not visible to us. If our eyes could tune into the waves of invisible frequencies, all electronic objects will not only look different but their borders will spread much wider, merging with other objects. The perception of the world will change. A new physical environment called Hertz space will be formed.


It is important to note that Hertz space is real and is on our side of monitors and screens, unlike virtual space, which is stored on servers all over the world and is still transmitted by cables in the ocean. Hertz space is an invisible medium for transferring informatio - Wi-Fi, 3G, GSM, radio. Hertz-space is real, and it is everywhere, like an invisible string of wires with its “electric climate” and “electrogeography”.
Using this shirt and effortlessly adding
Hertzspace to your personal space, you
unwittingly come across privacy issues,
because Hertzspace is highly militarized
and does not belong to us. Thus, the
speculatively made-up, absurd, at first
glance, the story turns out to be a reality
and allows you to look at the concept of
privacy and familiar things around in a
different way.
When Object Dream Shirt
Another critical object, “When Object Dream Shirt,” allows you to feel the invisible, but tangible warmth o the dreams of electrical appliances around. All smart appliances that are in “sleep mode” emit electro waves of a certain spectrum. Their dreams are made of electromagnetic radiation, which creates an invisible but physical environment when objects dream in a dream. Wearing a shirt, you can feel this environment and the dreams by electrical appliances.
![]()
When Object Dream Shirt
Another critical object, “When Object Dream Shirt,” allows you to feel the invisible, but tangible warmth o the dreams of electrical appliances around. All smart appliances that are in “sleep mode” emit electro waves of a certain spectrum. Their dreams are made of electromagnetic radiation, which creates an invisible but physical environment when objects dream in a dream. Wearing a shirt, you can feel this environment and the dreams by electrical appliances.

When objects dream shirt. Use to feel invisible but physical warmth by electric
appliances
Shirt, cotton, silkscreen. link
It seems cute and ridiculous. But if you learn about the malicious chatbot Mirai, which cracks user kettles, routers and webcams, going through a bunch of factory passwords, because very few people change them on such devices, the shirt takes on a new meaning. Infected devices continue to function normally, with the exception of some periodic slowness. After becoming “infected”, the device can send requests, for example, to the site.
![]()
This is called DDoS attack. While you
are drinking tea, your kettle, along with
other millions of kettles, is attacking
the New York Times website while
sending inquiries to it. The site fails to function and shuts down due to
technical problems. On January 14,
2018, a new version of Mirai was found,
focused on devices based on Argonaut
RISC Core processors, supplied in
more than 1.5 billion products a year,
including desktop computers, servers,
radios, cameras, mobile phones service
counters, televisions, storage devices,
network devices (smart hubs, TV
modems, routers, Wi-Fi) and objects of
the Internet of things.
Shirt, cotton, silkscreen. link
It seems cute and ridiculous. But if you learn about the malicious chatbot Mirai, which cracks user kettles, routers and webcams, going through a bunch of factory passwords, because very few people change them on such devices, the shirt takes on a new meaning. Infected devices continue to function normally, with the exception of some periodic slowness. After becoming “infected”, the device can send requests, for example, to the site.

Artist project. Prey. Data - is a new oil.
About privacy, security and our network experience.
Program for removing geolocation data, wi-fi connection data, device used info, camera photos, screenshot from laptop, Video. 2016. Anton Bundenko, link
Absurdity and reality mix. Sci-fi - Sci-Real.
When functional objects of functional
design are added to critical invented
objects, with functions that not yet
exist, absurdity and reality are finally
mixed together.
Functional design really works. The first of the functional design objects was assembled in the framework of the first theme of the project, concerning preventive processes and targeting, as well as affecting the concepts of physical and digital, free time and luxury in the age of information.
In the world of ubiquitous connection, free time and attention are becoming a luxury [4].
When functional objects of functional
design are added to critical invented
objects, with functions that not yet
exist, absurdity and reality are finally
mixed together.
Functional design really works. The first of the functional design objects was assembled in the framework of the first theme of the project, concerning preventive processes and targeting, as well as affecting the concepts of physical and digital, free time and luxury in the age of information.
In the world of ubiquitous connection, free time and attention are becoming a luxury [4].
The easy access to the global network has increased the average
workweek and dispersed attention.
Everyone at least once was ignored by
a friend or relative, too absorbed in a
smartphone or tablet. Someone was
exhausted by technology, multitasking
and constant connection.
![]()
When connection becomes an integral part of life along with the development of the Internet of things, preventive personalization processes, computer vision and identification processes – the possibility of being offline at times, like the concept of privacy, will become a luxury.

When connection becomes an integral part of life along with the development of the Internet of things, preventive personalization processes, computer vision and identification processes – the possibility of being offline at times, like the concept of privacy, will become a luxury.
For temporary outages, special
gadgets will be used to block the radio,
cellular communications, Wi-Fi,
Bluetooth, geolocation definitions and
remote monitoring.
![]() For these purposes there is a pocket
blocking all electromagnetic waves
from civil to military and allowing you
to completely distance yourself from
your gadgets and external processes.
Protection from hidden globalization
processes, information flows and
constant switching on is provided
For these purposes there is a pocket
blocking all electromagnetic waves
from civil to military and allowing you
to completely distance yourself from
your gadgets and external processes.
Protection from hidden globalization
processes, information flows and
constant switching on is provided
by temporary outages and rest from the atmosphere of large megacities, immersion in yourself, listening to internal rhythms, communication with friends, and visual-tactile contact in the physical space with the person selected for joint immersion. Protection against unauthorized hacking of Paypass and other contactless cards in public spaces. Protection against reading geolocation and territorial targeting.

by temporary outages and rest from the atmosphere of large megacities, immersion in yourself, listening to internal rhythms, communication with friends, and visual-tactile contact in the physical space with the person selected for joint immersion. Protection against unauthorized hacking of Paypass and other contactless cards in public spaces. Protection against reading geolocation and territorial targeting.
At a business meeting, in order to show
respect for your partner and show that your conversation will remain
between you, you put your phone in your blocking pocket. These are
exclusively ethical issues that are rooted
in handshakes and clinking glasses of
wine. When meeting with your other
half, both of you put the distracting
gadgets in your pocket and this way you
tell each other that you are here, in the
moment, in the physical space, your
attention belongs only to her/him,
here and now. These are very interesting
user experiences, the need for which
will grow. Ever since the times when the clinking of glasses was formed as a
sign of trust in each other (when wine
is poured from glass to glass - you are confident that your acquaintance
did not pour poison into your wine), demonstrative shielding of gadgets
during business meetings and close
communication can also be perceived
as ethical gestures of the information
technology era.
About privacy, security and our network experience.
Program for removing geolocation data, wi-fi connection data, device used info, camera photos, screenshot from laptop, Video. 2016. Anton Bundenko, link
Thinker. Futureisnown community.
In the nearest future the interest towards technology will continue to grow as technology influences our lives more and more each day. At
times we through a series of “Thinker” parties, attended by the people who are interested in technological processes or are related to studying or working with them. Technology should not be perceived as boring and for geeks only, it is exciting and important. We want more people to become aware of it.
We are networking through different mediums, we see the surrounding contexts as reality and we are learning to work with it. It is essential for us to inform others about new reality,
In the nearest future the interest towards technology will continue to grow as technology influences our lives more and more each day. At
times we through a series of “Thinker” parties, attended by the people who are interested in technological processes or are related to studying or working with them. Technology should not be perceived as boring and for geeks only, it is exciting and important. We want more people to become aware of it.
We are networking through different mediums, we see the surrounding contexts as reality and we are learning to work with it. It is essential for us to inform others about new reality,
focus
on critical thinking and create objects
in order to do it. You can call it the new
cosmism, digital awareness, speculative
actionism, critical design or speculative art.
Today we are travelling to Latin America and we have to adapt our ideas to the language used by locals.
Due to prolongations made by local socio-political departments, we put on Electrosmog shirts to stay safe from aggressive electro geography, we bring a couple of informational sweatshirts and vandal stickers with us. We pack safe data transfer belts, additional blocking devices and digital storytellers. I turn off the speculative program of my home, sleep and yesterday’s dreams.
Today we are travelling to Latin America and we have to adapt our ideas to the language used by locals.
Due to prolongations made by local socio-political departments, we put on Electrosmog shirts to stay safe from aggressive electro geography, we bring a couple of informational sweatshirts and vandal stickers with us. We pack safe data transfer belts, additional blocking devices and digital storytellers. I turn off the speculative program of my home, sleep and yesterday’s dreams.
NOTES:
1 Website Europe versus Facebook found via http://europe-v-facebook.org/ EN/en.html. May 9, 2018.
2 Duportail J. I Asked Tinder for
My Data. It Sent Me 800 Pages of
My Deepest, Darkest Secrets // The Guardian, September 26, 2017.
3 Bundenko А. Future Is Nown // artist’s web page, https://futureisnown. com/futureisnown/.
4 Bundenko А. Entering the Pause // artist’s web page, https://futureisnown. com/entering-the-pause/.
1 Website Europe versus Facebook found via http://europe-v-facebook.org/ EN/en.html. May 9, 2018.
2 Duportail J. I Asked Tinder for
My Data. It Sent Me 800 Pages of
My Deepest, Darkest Secrets // The Guardian, September 26, 2017.
3 Bundenko А. Future Is Nown // artist’s web page, https://futureisnown. com/futureisnown/.
4 Bundenko А. Entering the Pause // artist’s web page, https://futureisnown. com/entering-the-pause/.
Anton Bundenko, 2018
Bundenko was born in Abakan (Hakasya) in 1989, currently residing in Bishkek, Istanbul, Moscow. He i an artist, working on Futureisnown since 2016. The project is dedicated to prototyping in digital era, its impact on social discourse and critical thinking.
Bundenko was born in Abakan (Hakasya) in 1989, currently residing in Bishkek, Istanbul, Moscow. He i an artist, working on Futureisnown since 2016. The project is dedicated to prototyping in digital era, its impact on social discourse and critical thinking.
Futureisnwn, Bundenko, 2018
Air-store
presentation
Futureisnwn, Bundenko, 2018
Air-store Futureisnown
exhposition
Design (Futureisnown) Collection:




















About privacy, security and our network experience.
Program for removing geolocation data, wi-fi connection data, device used info, camera photos, screenshot from laptop, Video. 2016. Anton Bundenko, link
or Speculative objects position

Anton Bundenko
Object design, Merch
Graphic design
Visual production
Tech-Art solutions
Art with ai for interior and exterior
Augmented reality
Neural networks
Object design, Merch
Graphic design
Visual production
Tech-Art solutions
Art with ai for interior and exterior
Augmented reality
Neural networks
Productions:
About
Studio
Production
Distribution
Career
About
Studio
Production
Distribution
Career
Links:
Media
Press
Downloads
Media
Press
Downloads
+79-057-193-600 ( telegram )
+996-507-740-436
bundenko@gmail.com. ︎
︎ ︎ ︎ ︎
![]() Are.na
Are.na
+996-507-740-436
bundenko@gmail.com. ︎
︎ ︎ ︎ ︎
